
For any organization handling cardholder data (CHD), the Payment Card Industry Data Security Standard (PCI DSS) is a daunting but necessary framework. As of 2026, with the full adoption of PCI DSS v4.0.x, the complexity of maintaining compliance has only increased. One of the most effective strategies to manage this burden—both financially and operationally—is PCI DSS scope reduction.
By implementing robust network segmentation, organizations can isolate sensitive data, minimize the “attack surface,” and significantly decrease the number of systems that must meet stringent audit requirements.
Understanding the “Scope” Problem
In the eyes of a PCI Qualified Security Assessor (QSA), your “scope” includes every person, process, and technology that stores, processes, or transmits cardholder data. However, it doesn’t stop there. It also includes any system that can impact the security of that data.
Without segmentation, a single guest Wi-Fi router or an office printer could technically be “in scope” if they sit on the same flat network as your point-of-sale (POS) system. This leads to:
-
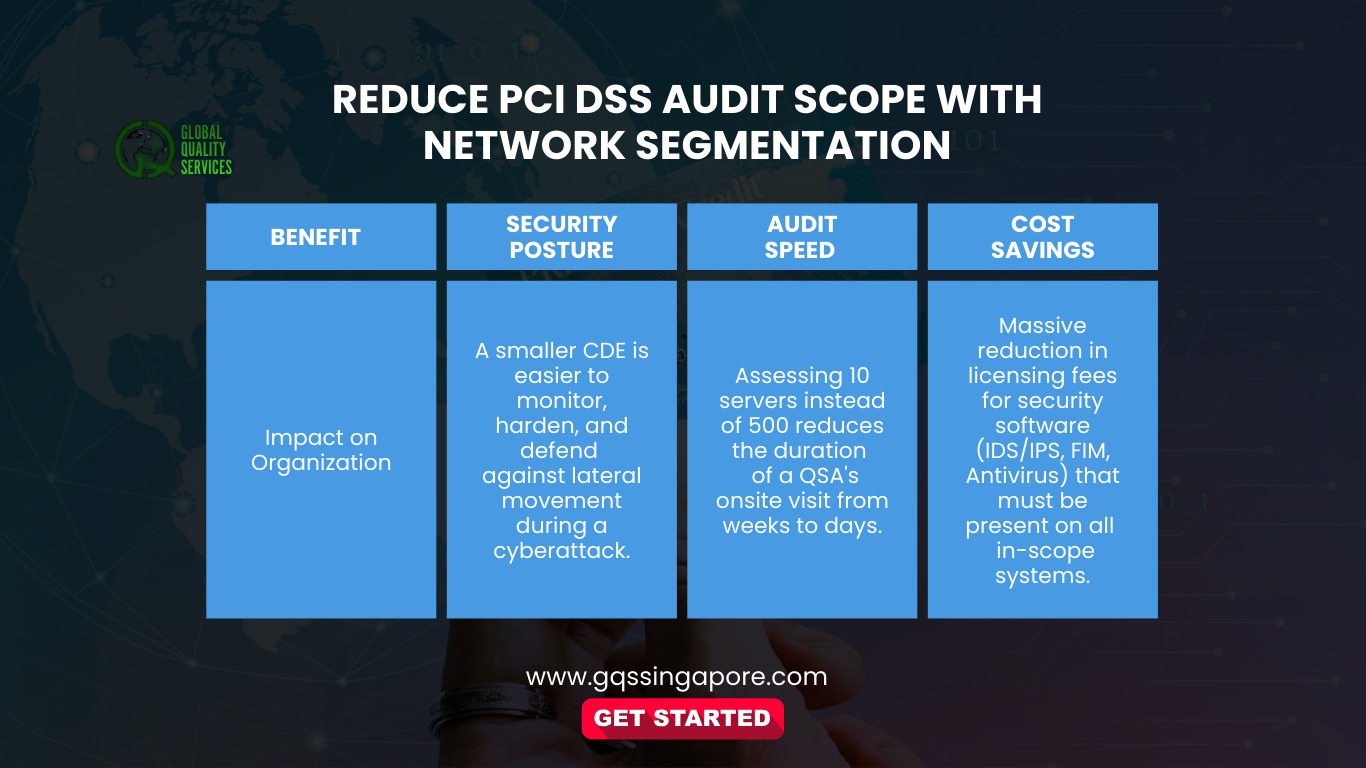
Inflated Audit Costs: More systems to test means more hours for the QSA.
-
Increased Risk: A breach in a non-secure area can pivot to the cardholder data environment (CDE).
-
Operational Fatigue: Applying high-level security patches to non-critical systems just to satisfy a checklist.
How Network Segmentation Works for Scope Reduction
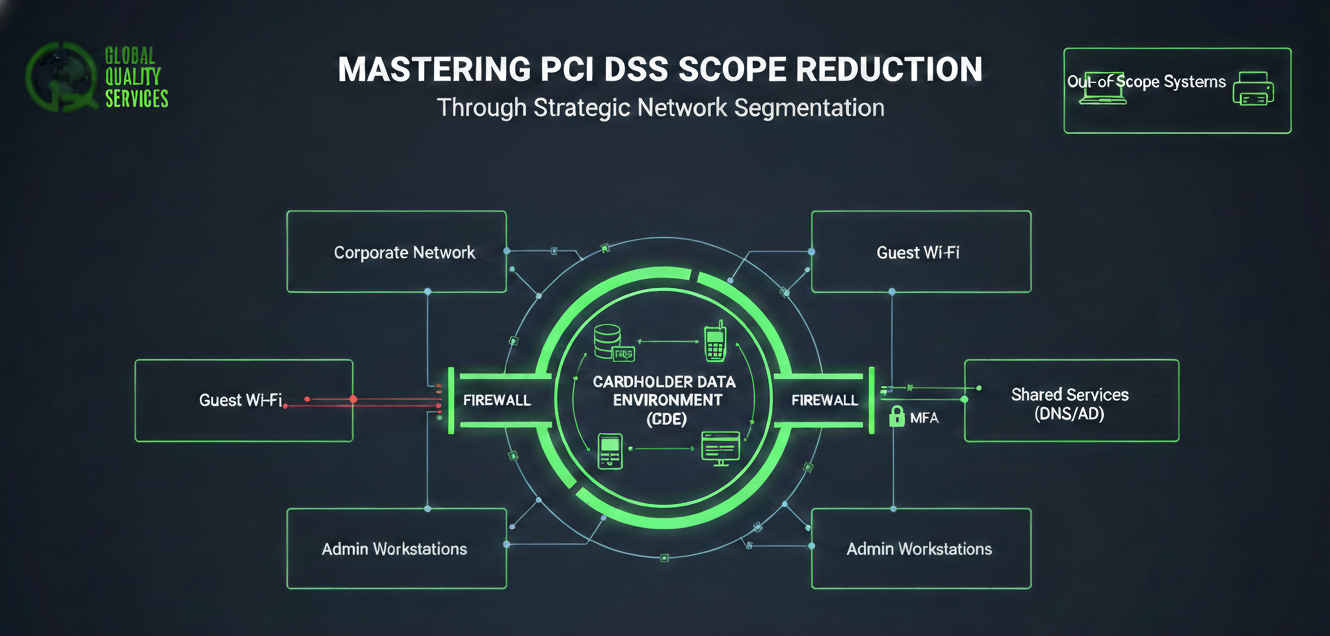
Network segmentation is the practice of splitting a computer network into smaller subnetworks (segments). When done correctly for PCI, it creates a “digital fortress” around your Cardholder Data Environment (CDE).
1. Defining the Cardholder Data Environment (CDE)
The CDE is the heart of your compliance efforts. It consists of the system components that handle CHD or sensitive authentication data. The goal of segmentation is to ensure that systems outside the CDE cannot communicate with systems inside the CDE unless explicitly required and strictly controlled.
2. The Role of Firewalls and VLANs
Segmentation is typically achieved through:
-
Hardware Firewalls: Acting as the gatekeeper between the CDE and the rest of the corporate network.
-
Virtual Local Area Networks (VLANs): Logically separating traffic at the switch level.
-
Access Control Lists (ACLs): Defining exactly which IP addresses and ports are allowed to talk to one another.
3. The “Out-of-Scope” Criteria
To successfully claim a system is out of scope via segmentation, it must meet three criteria:
-
It does not store, process, or transmit CHD.
-
It is not on the same network segment or VLAN as the CDE.
-
It cannot connect to or influence the security of the CDE.
Step-by-Step Guide to Implementing PCI DSS Scope Reduction
Reducing your audit footprint isn’t a one-time project; it’s a strategic re-architecting of your data flow.
Phase 1: Data Discovery and Flow Mapping
You cannot protect what you don’t know exists. Use automated discovery tools to find where CHD is hiding in your network.
-
Identify all ingress points: Where does data enter (e.g., web forms, physical terminals)?
-
Identify storage points: Is data being logged in error reports or database backups?
-
Map the journey: Draw a clear diagram of how data moves from the point of entry to the merchant bank.
Phase 2: Isolation of the CDE
Once the data flow is mapped, use “Zero Trust” principles to isolate those systems.
-
Physical or Logical Separation: While physical separation (separate hardware) is the gold standard, logical separation (VLANs and firewalls) is the industry norm and is fully accepted by the PCI Council if configured correctly.
-
Eliminate Unnecessary Connections: If your HR payroll system doesn’t need to talk to your payment gateway, block that path entirely.
Phase 3: Implement Strong Access Control
For the few systems that must communicate with the CDE (like a jump server for administrative access), implement Multi-Factor Authentication (MFA). Under PCI DSS 4.0, MFA is non-negotiable for all access into the CDE.
The Benefits of a Reduced Scope
Focusing on PCI DSS scope reduction provides immediate ROI in three specific areas:
Common Pitfalls in Segmentation
Even with the best intentions, organizations often fail their audits due to “scope creep.” Watch out for these common mistakes:
1. Shared Services
A common mistake is hosting shared services—like DNS, NTP, or Active Directory—on a general network that the CDE relies on. If the CDE depends on a server for its security or functionality, that server is pulled into scope.
-
Solution: Create dedicated “Security Impact” segments for these services or harden them to CDE standards.
2. Misconfigured Firewalls
A single “Permit Any” rule in a firewall config can invalidate your entire segmentation strategy. QSAs will look for “leaky” segments where traffic from a low-security zone (like a breakroom Wi-Fi) can reach a high-security zone.
3. Forgetting the “Human” Element
Scope isn’t just hardware. If your IT admins use the same workstations to browse the web and manage the CDE, those workstations are in scope.
-
Solution: Use dedicated Administrative Workstations or highly secured Jump Boxes.
The Role of Modern Technologies: Tokenization and P2PE
While network segmentation is a networking solution, you can further your pci dss scope reduction efforts by using data-centric solutions:
-
Point-to-Point Encryption (P2PE): If data is encrypted the moment it hits a physical terminal and is only decrypted by the processor, the merchant’s network never “sees” the raw data. This can reduce the Self-Assessment Questionnaire (SAQ) from hundreds of requirements to just a few dozen.
-
Tokenization: Replacing raw credit card numbers with “tokens” means your internal databases no longer hold CHD. If you don’t store the data, the systems storing the tokens may move out of scope.
Maintenance: The “Set it and Forget it” Myth
PCI DSS Requirement 11.4.5 (in version 4.0) emphasizes that segmentation controls must be tested regularly. You cannot simply set up a firewall and assume it works forever.
-
Annual Penetration Testing: You must perform “segmentation checks” at least once a year (and after any significant change) to prove that your out-of-scope zones truly cannot reach the CDE.
-
Continuous Monitoring: Use automated tools to alert you if a new device is plugged into a CDE switch or if a firewall rule is modified.
Achieving pci dss scope reduction through network segmentation is the single most effective way to simplify compliance. It transforms a sprawling, unmanageable audit into a focused, surgical exercise. By isolating your Cardholder Data Environment, you not only save money and time but also build a more resilient defense against the evolving landscape of financial cybercrime.
In 2026, compliance isn’t just about passing an audit, it’s about verifying that your boundaries are impenetrable. Contact Global Quality Services to know more
